Kenric, I want to address your thoughts here in different aspects: first clarifying the ACF edition difference you observed, then discussing the technical underpinnings (for your question about Lucee), also sharing some sad prospects to consider. But then I want to address your assertion that the lack of Sandbox Security is inherently a “vulnerability”, and finally offer some more alternatives as you’ve asked.
1: First, while realize that many resources (including from Adobe) indicate that Sandbox Security is Enterprise-only, in fact it was made available in CF Standard starting with CF11, which came out in 2014.
Before anyone may think I’m confusing this with the “Resource Security” feature (which CF Standard had before that–essentially allowing one sandbox configuration for the entire instance), that is NOT what I’m referring to. That, too, was removed with CF11, and now Standard has the same Sandbox Security feature that Enterprise had.
(I do realize of course many people here may have stopped paying attention to CF differences long ago, when they switched to Lucee. I live and breath clarifying these differences about CF editions and versions in my work and presentations, and I even have a talk on differences between CF Ent and Std, where I also shared this news about Sandbox .)
And to be clear this change IS documented, on the CF doc page about security features in the CF Admin, where it notes that “In ColdFusion 11, you can configure multiple security sandboxes irrespective of the edition that you are using.” (Sadly there are 5 other references on that page to the old distinction of Standard. There are other pages on Adobe’s site that also were never updated.)
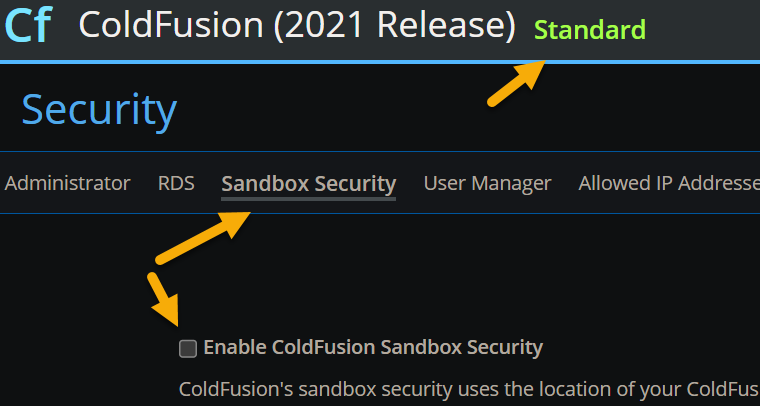
Finally, FWIW I’ve attached below a screenshot from a cf2021 Standard edition which I have running, showing that this is no mistake that the docs (or I) say this.
2: So now, about those technical underpinnings of the sandbox feature, and your hope of seeing it perhaps added to Lucee, I’ll note that the feature is (and always has been) based on the underlying Java Security Manager feature.
So COULD Lucee provide for it? Sure. It’s not depending on some licensed software, which is perhaps what you thought the Enterprise limitation was implying.
But will the Lucee team take it on? I won’t be surprised if it’s a “hard pass”.
3: And one reason will be that folks who follow Java may have pricked up their ears at what I just said, as they’ve heard that the Java leadership and many in the community have been targeting complete removal of the Security Manager from Java. It’s currently “deprecated”, as they await community feedback.
Their beef (I’m paraphrasing) is that “no one uses it”, and it’s “hard to keep dealing with it”–and the worse is that most assume “it’s only of value for client-side java, which is hardly used any more”. But they won’t care to hear much from CF folks saying, “wait, we use it”.  My hope is that some other large java project ALSO uses it for server-side security and will get their ear and plead for a stay of execution.
My hope is that some other large java project ALSO uses it for server-side security and will get their ear and plead for a stay of execution.
Indeed, here you are singing its praises–which are deserved…but very few in the CF/Lucee world know of it, and fewer use it–which is indeed sad. (I’ve spoken on it, and I even wrote a two-part series on it for for Adobe…um…22 years ago. FWIW, you can still read it and for better or worse the feature hasn’t changed much since then!)
4: Moving on, you bring this up in the guise of the lack of it existing in Lucee being a “vulnerability in shared hosting environments” that should “have been mentioned” in the Lucee security docs.
I’m not sure I’d cast it quite as a vulnerability. It’s more an inherent limitation of shared hosting–and a reason why it’s gone the way of the dodo mostly. You bring up Docker as an alternative, but there are others. Since you wondered about possibilities you may consider, here are a few others.
5: I’ll note first that most hosting companies in the CF space switched to vps’s (virtual private servers) a long time ago, where each client had what SEEMED to them to be their “own server”. In that case, it was OS software or otherwise that implemented the separation you rightly are concerned to see.
Others solve the separation problem with vm’s.
And some might propose that one CAN run multiple instances of Lucee, each with their own JVM–which can run as a different user. And then you can control via the OS what folders that user can access.
6: Then again, controlling file access is really only one facet of sandbox security. As you may have read, it also affords control over much more, such as what datasources can be used, what tags can be called, what domains/ips and ports can be called, and much more.
It may also be worth clarifying that the sandbox security feature was not really about controlling “who could see what” based on the “user” running the CF instance–instead it was about “what code could see/do what” based on where that code lived. It was set “per folder”–which was “the sandbox” to be configured. Again, anyone curious to understand it more can see my article (or the Adobe docs) for more.
It was a nifty feature–though it had its warts, and some special massaging it sometimes needed as certain aspects of CF configuration and the JVM evolved over time. I never got around to doing something on that, but I know others did, including Snake in 2006, and Adam Cameron in 2013, and a few folks in a Farcry thread in 2020 (which concluded with a seeming fix Adobe was applying in CF2018 then).
I realize this is now getting into the weeds–as it’s how it worked on ACF. I just share it to help both those who may explore it in ACF…and as more fodder for any who might consider it for Lucee.
And here’s that image of it running in CF Standard, FWIW: